The Ultimate Command Center
The real time monitoring and control platform tool ensures continuous oversight of critical operations.
Whether in Oil & Gas facilities, helipads, or emergency operations, the system ensures that every activity is monitored, recorded, and protected against tampering, enabling faster response times and increased operational safety.
Deploy a fully powered control room in minutes
With an intuitive dashboard, operators can monitor, analyze, and control critical infrastructure effortlessly. Hardware integration is seamless and ergonomic, supporting multiple screens, and remote access, reducing operator fatigue while enhancing productivity and situational awareness. The embedded AI functions provide extra power to operators supporting their daily routinary work and ensuring that the human-error goes to zero.
Leverages AI and Blockchain to protect critical infrastructure data from cyber threats
Real-time tracking and automated alerts
Integrated with Air Traffic Control (ATC) and Unmanned Traffic Management (UTM)
AI-driven facial recognition and prevent unauthorized access and security breaches
Monitors electrical systems, fire safety, and emergency power
Redundant communication networks for emergency response and remote coordination
Tracking accurate positioning, flight safety, and operational efficiency
A tight integration between software and hardware is crucial. Without deep integration, delays, data mismatches, or system vulnerabilities could compromise flight safety, infrastructure security, and mission-critical operations.
The images displayed are actual screenshots of OilChain’s software, showcasing a direct look at how the system operates.
Aircraft Identification & Status
- ICAO Address / Tail Number – Unique identifier for each aircraft.
- Call Sign – Flight identification used by ATC and pilots.
- Flight Plan Information – Departure, destination, and route details.
- Operator Information – Airline, military, or private ownership details.


Position & Movement Data
- Latitude & Longitude (GPS Positioning) – Real-time location tracking.
- Altitude (Barometric & Geometric) – Height above sea level or ground level.
- Speed (Ground Speed & Airspeed) – Velocity of the aircraft.
- Heading (Track Angle & Bearing) – Direction of flight.
- Vertical Rate (Climb/Descent Speed) – Rate of altitude change.
Airspace & Navigation Parameters
- ADS-B Data (Automatic Dependent Surveillance–Broadcast) – Live position and intent broadcasting for cooperative aircraft.
- Radar Detection (4D Radar, Multifrequency Tracking) – Identification of non-cooperative aircraft or drones.
- UTM & ATC Clearance Information – Permissions for controlled airspace access.
- No-Fly Zones & Geo-Fencing Alerts – Restrictions and warnings for unauthorized zones.
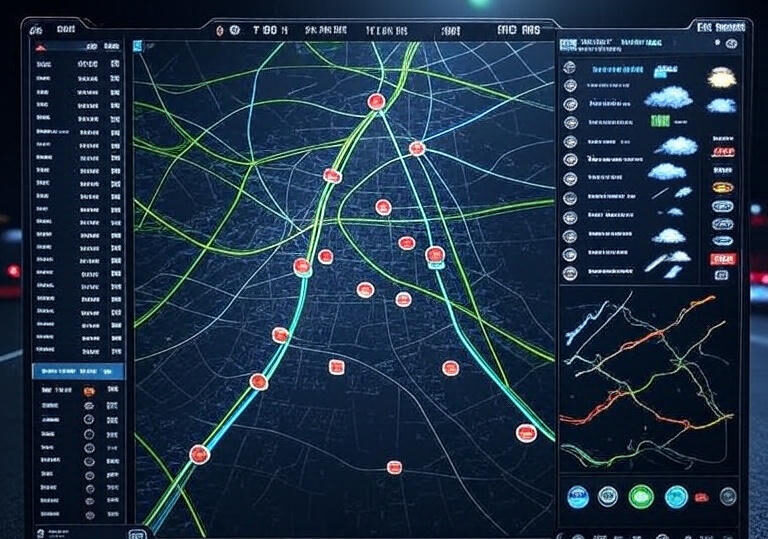
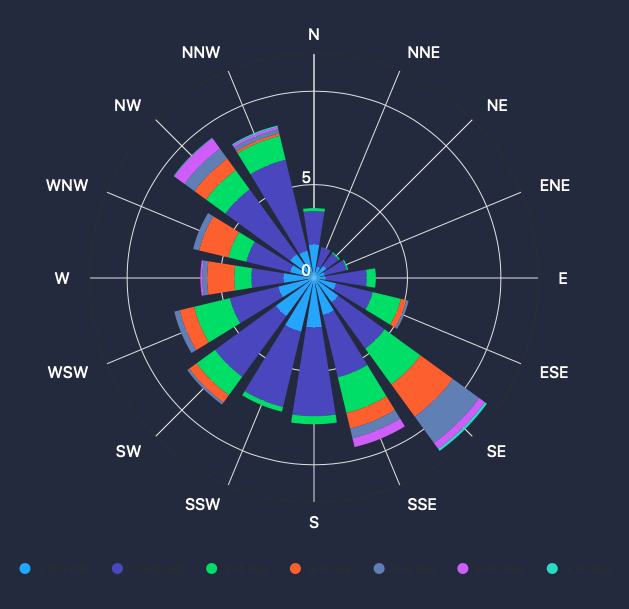
Environmental & Safety Monitoring
- Weather Conditions (Wind, Visibility, Temperature) – Real-time atmospheric data.
- Obstacle & Collision Detection (LIDAR & Thermal Sensors) – Identifies potential hazards.
- Battery & Fuel Levels (For eVTOLs & Drones) – Ensures mission continuity.
- Intrusion & Cybersecurity Alerts (Blockchain Authentication) – Prevents spoofing and unauthorized flight path deviations.
SCT - Smart Control Tower
The SCT is a fully automated, plug-and-play, AI-powered monitoring system designed to provide real-time airspace awareness, flight coordination, and infrastructure security.

Optimally placed in strategic locations that maximize airspace visibility
Built for helipads, vertiports, emergency landing and high-security zones, it seamlessly integrates weather tracking, obstacle detection, and automated air traffic management into a single, autonomous unit.
The First Transportable Plug and Play System
Plug&Play structure and user friendly to activate.
Few hours to install and SCT is online.
Minimum footprint on the ground.
Reduces the supply chain of technical teams.
Direct communication & Mobile devices supported.
Data always available in real time & Cyber attacks risk-free.
Helipads & Vertiports
Positioned near landing/takeoff zones to ensure real-time flight coordination, obstacle detection, and automated lighting control.
Airports & Remote Airstrips
Enhances situational awareness and flight safety, especially in areas with high air traffic or low-altitude operations.
Industrial & High-Security Areas
Monitors unauthorized drone activity, airspace security, and infrastructure integrity.
Oil, Gas and Energy Facilities
Provides secure airspace monitoring, control and landing assistance for helicopters transporting personnel or cargo.
Emergency & Medical Response Sites
Ensures safe and efficient helicopter landings in hospitals, disaster zones, and search-and-rescue operations.
Military & Law Enforcement Bases
Supports secure airspace management, rapid deployment, and surveillance of restricted zones for defense and security operations.
720 degrees situational awareness for potential threats anticipation
Unlike traditional systems limited to a single direction, Smart Control Towers continuously monitors 360° around its location and 360° in vertical airspace, detecting aircraft, drones, and environmental conditions from every possible angle.
MULTI-NODES Infrastructure for Interconnected systems
Each node is a fully automated station which operates standing alone and in an interconnected mode inside a closed network, providing one another, pilots and control operators with crucial information on usability, weather conditions, system flaws and more about any Helipad or Vertiport.
High scalability, Redundancy & Failover Protection
Nodes can be deployed individually or as a network allowing expansion based on site-specific needs. If one node goes offline, the system automatically re-routes data to maintain uninterrupted coverage.
Designed to be Indestructible
Designed for harsh environments, Smart CT nodes feature energy-efficient components, solar compatibility, and ruggedized enclosures for continuous operation.
Security & Anti-Tampering Measures
The hardware is designed with tamper-proof casing, environmental shielding, and automated alerts to detect and report physical intrusion attempts. Only authorized personnel can access the system through multi-factor authentication (MFA), biometric verification, and role-based permissions.